It is best practice to enable AWS multi-factor authentication while interfacing with AWS via the CLI or SDK. This procedure assumes that you already have an AWS user account with an MFA device enabled. Click here if you do not. The steps below outline how to enable MFA using the aws-mfa software.
Main Steps:
- Install
aws-mfa - Set up your
~/.aws/credentialsfile - Run command to connect
Installation
To install aws-mfa, run the command in your terminal:
pip install aws-mfaSet Up AWS Credentials File
If you’ve ever ran aws configure before, the credentials file, ~/.aws/credentials , will already exist. Open this file with using a command-line text editor, such as vim:
vim ~/.aws/credentialsNext, add the suffix, “-long-term” to all your existing profile names. For example, change “[default]” to “[default-long-term]”. Your access key and secret key should have been provided to you by your administrator at the time of your account creation.. Also, if you have ran aws configure in the past, this may already be populated. If you have not, please enter your credentials here. Each profile will correspond with one set of user credentials.
Before:
[default]
aws_access_key_id = YOUR_ACCESS_KEY_ID
aws_secret_access_key = YOUR_SECRET_ACCESS_KEY
[dev]
aws_access_key_id = YOUR_ACCESS_KEY_ID
aws_secret_access_key = YOUR_SECRET_ACCESS_KEY
After:
[default-long-term]
aws_access_key_id = YOUR_ACCESS_KEY_ID
aws_secret_access_key = YOUR_SECRET_ACCESS_KEY
[dev-long-term]
aws_access_key_id = YOUR_ACCESS_KEY_ID
aws_secret_access_key = YOUR_SECRET_ACCESS_KEYThat is the only modification you will need to manually make to the credentials file. After you run the aws-mfa command, short term credentials and a temporary security token will be automatically populated.
Run the aws-mfa command
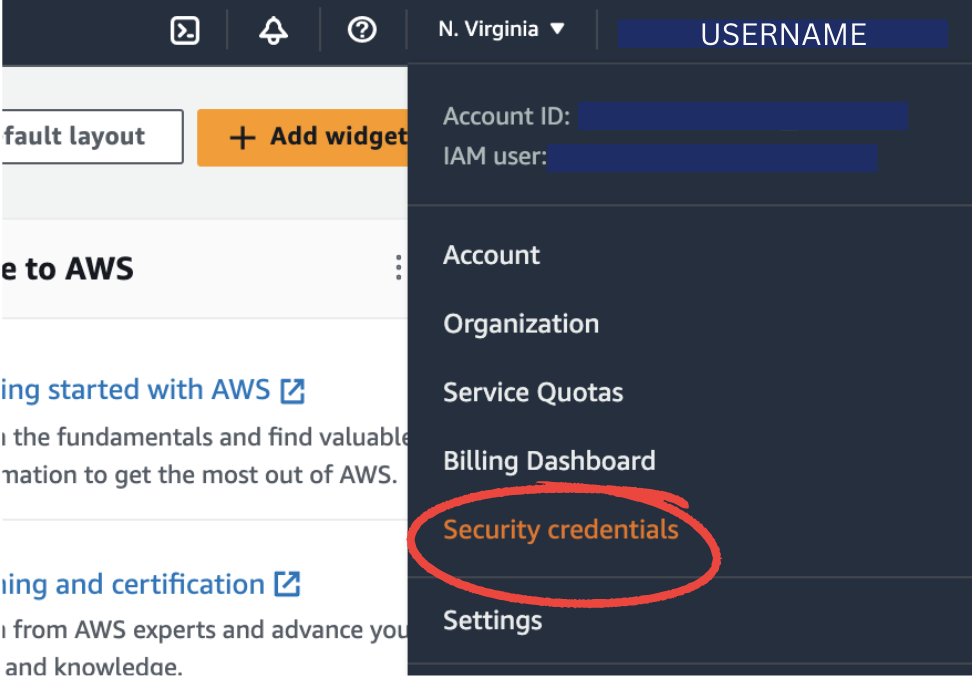
Navigate to the AWS Console and click on your username on the top right corner. Then, select “Security credentials”.
In the AWS IAM Credentials tab, under the Multi-factor authentication (MFA) section, copy the ARN identifier of your assigned MFA device.
For example: arn:aws:iam::<account-number>:mfa/<username>
Run the command to connect:
aws-mfa --device {MFA_DEVICE_ARN}You will then be prompted to enter your passcode from the respective MFA device. Enter the code and you are done!
Note that you will be connected for the default time of 12 hours. The maximum time to connect is 36 hours. Next time you can simply use the --duration <time-in-seconds> to extend your connect time.
For example: aws-mfa --device {MFA_DEVICE_ARN} --duration 129600
Additional Helpful Resources:
Click here to report typos.